This is an analysis of malware from a fellow Marine @huskyhacks who teaches malware analysis. Figured it would be good to share and show some simple analysis of malware. But this is all from him so go check out his great work!
Here is a list of tools you can use, this is not all-encompassing as there are many ways to skin a cat
Tools
Basic Analysis:
File hashes
VirusTotal
FLOSS
PEStudio
PEView
Wireshark
Inetsim
Netcat
TCPView
Procmon
Advanced Analysis:
Cutter
Debugger
Preface:
"Analyst,
This specimen came from a poor decision and a link that should not have been clicked on. No surprises there. We need to figure out the extent of what this thing can do. It looks a little advanced.
Perform a full analysis and send us the report when done. We need to go in-depth on this one to determine what it is doing, so break out your decompiler and debugger and get to work!
IR Team"
Objective:
Use all of the tools at our disposal to analyze the sample and gather the information we will need to understand the threat actor and their capabilities and TTPs:
So first off, I am using the FlareVM for the analysis and a REMnux box for packet inspection and dynamic network analysis. FlareVM has an internal tool to create a fake network setup if you need it. It's important to note that none of this is networked to the host machine and done in a sterile lab environment. Shoutout to safety!
Initially, I want to learn basic information about the binary in question, like what language it is written in, hashes, VirusTotal results, etc. You can use simple commands like certutil and pull the MD5 or SHA256 values
Once you have the hash, you can find out a lot about the binary simply through open-source research done by others. Going to sites like VirusTotal or automated malware analysis sites like Triage where you can search by filehash value, can give you a lot of information about the binary already. However, it is essential to note that more advanced malware is written to avoid these automated sandboxes and will not deploy unless the host has a specific screen size or memory allocation. Similar to Russian malware not deploying on hosts with Russian keyboards installed
From these automated results, we can begin to answer some basic questions like:
What language is the binary written and what is the architecture: This is an x64 64bit executable for MS Windows (GUI) Mono/.Net assembly written in nim which compiles to C. C++, and Java
Or, if you want to use tools on the FlareVM, such as PEStudio or Cutter, you can find the same results.
An interesting note about this binary is that if the binary cannot connect to an outside address, it will delete itself after detonation. The goal of the binary is to call back to a specific external C2 address; if that address does not connect, it will simply delete itself without harming the system.
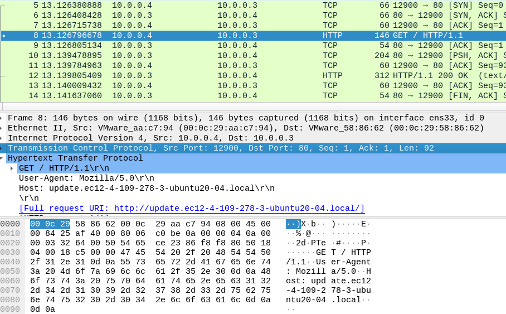
There is no persistence in this binary even though it does reach out to C2 servers, as you can see below,
The first callback domain is update.ec12-4-109-278-3-ubuntu20-04.local , as can be seen here in Wireshark on our REMnux box
This binary will also exfil data if it can connect to a secondary address hxxp://cdn.altimiter.local in this case. It either encrypts or encodes the data and sends it out via GET request using a post method to write to a log in the domain. Because it is either encrypted or encoded we will need to figure out how and with what algorithm
After looking through strings output from Floss we can find that RC4 encryption is in use. Also as we explore through Procmon we will see that a file is created in the public folder called Password.txt, which contains the password to decrypt the RC4 encoded data.
As you can see, there is a process called Houdini, which is what causes the program to delete itself and disappear if it can not find an outbound connection to its C2 server or if it is interrupted, or even completes itself









You should do this same level of analysis on shady companies/organizations.